Difference between revisions of "DMVPN Service Provider"
Jump to navigation
Jump to search
(Created page with "This is a design for a DMVPN/FlexVPN using Cisco IOS-XE. = Goals = [X] - functional [-] - testing, but not working [ ] - to be worked on [X] DMVPN via the hub, no site...") |
(No difference)
|
Revision as of 14:13, 8 July 2025
This is a design for a DMVPN/FlexVPN using Cisco IOS-XE.
Goals
[X] - functional [-] - testing, but not working [ ] - to be worked on
[X] DMVPN via the hub, no site to site traffic [X] DMVPN - IKEv2 [X] DMVPN - aes 256 [X] iBGP between all nodes [X] iBGP label distribution [ ] BFD for tunnel interfaces [ ] BFD for BGP [ ] BFD for PIM [X] Multicast on the underlay [X] Multicast Underlay - anycast RP [X] L3VPN over BGP [-] L3VPN over BGP with multicast [-] L3VPN w/mcast - Anycast RP on Hubs [X] L3VPN local breakout via NAT [-] L3VPN local breakout via NAT - failover between FRONT-DOOR and CELL-DOOR VRFs [ ] L2VPN over BGP [ ] Failover between FRONT and CELL [ ] Failover between Core [ ] Load Balance between cores [ ] IPv6 DMVPN if needed [ ] Cellular interface setup [ ] Security hardening
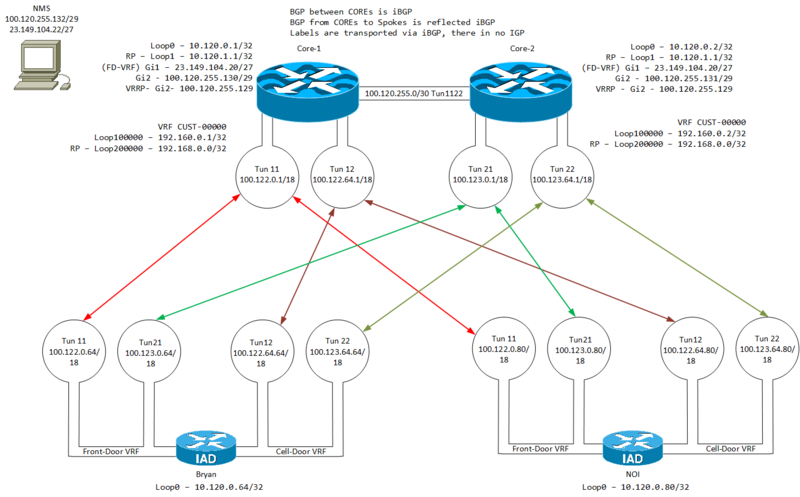
Diagram
Design
The basic design is: Core/P of 2 virtual routers running IOS-XE, each with two multi-point tunnels iBGP used for routing, with the cores as RR iBGP to distribute labels for MPLS global table is the DMVPN underlay only (100.64.0.0/10) FRONT-DOOR vrf for tunnels to the internet MGMT-VRF for management CUST-00000 - L3 VPN w/multicast (192.168.0.0/16) Edge CE/PE Two service provider VRF's iBGP sessions to each RR IBGP session to the RR loopback for MDT FRONT-DOOR for Ethernet uplink CELL-DOOR for 4g/5g uplink CUST-00000 - L3 VPN w/multicast (192.168.0.0/16) global table is the DMVPN underlay only PIM for underlay on tunnel interfaces All traffic routes via the core, no edge to edge breakout
configs
Core 1
version 17.12
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform sslvpn use-pd
platform console serial
!
hostname CORE-1
!
boot-start-marker
boot system bootflash:c8000v-universalk9.17.12.04a.SPA.bin
boot-end-marker
!
!
vrf definition CUST-00000
description Customer 00000 - Mvpn for DAMM radios
ipv4 multicast multitopology
rd 64512:0
route-target export 64512:100000
route-target import 64512:100000
!
address-family ipv4
mdt default 232.0.1.69
bgp next-hop Loopback0
exit-address-family
!
address-family ipv4 multicast
topology customer-000000
all-interfaces
!
exit-address-family
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication login vpnclient local
aaa authorization console
aaa authorization config-commands
aaa authorization exec default local
aaa authorization network localgroups local
!
aaa session-id common
no process cpu autoprofile hog
!
ip vrf FRONT-DOOR
description Front-Door VRF only for public
rd 62000:1
!
ip multicast-routing distributed
ip multicast-routing vrf CUST-00000 distributed
ip multicast longest-match
!
no ip domain lookup
ip domain name keekles.org
!
login on-failure log
login on-success log
!
subscriber templating
vtp version 1
!
mpls label mode all-vrfs protocol bgp-vpnv4 per-vrf
no mpls ip propagate-ttl
multilink bundle-name authenticated
!
license udi pid CSR1000V sn 9WCP1VOJDCN
license boot level ax
archive
log config
record rc
logging enable
logging size 400
path bootflash:archive/
maximum 14
time-period 5
memory free low-watermark processor 71477
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
username ${USER1} privilege 15 secret 9
!
redundancy
!
crypto ikev2 proposal IKEv2-VPN
encryption aes-cbc-256
integrity sha512
group 19
!
crypto ikev2 policy IKEv2-VPN-POLICY
match fvrf FRONT-DOOR
proposal IKEv2-VPN
!
crypto ikev2 keyring NOI-DMVPN
peer REMOTE-ROUTERS
description REMOTE-ROUTERS
address 0.0.0.0 0.0.0.0
pre-shared-key ${PSK}
!
!
crypto ikev2 profile IKEv2-VPN-PROFILE
match fvrf FRONT-DOOR
match address local 23.149.104.20
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local NOI-DMVPN
no lifetime certificate
ivrf FRONT-DOOR
!
crypto ikev2 fragmentation
!
cdp run
!
crypto ipsec transform-set AES256 esp-aes 256 esp-sha512-hmac
mode transport
!
crypto ipsec profile IPSEC-PROF-DMVPN
set transform-set AES256
set ikev2-profile IKEv2-VPN-PROFILE
!
crypto ipsec profile IPSEC-PROF-STATIC
set transform-set AES256
set ikev2-profile IKEv2-VPN-PROFILE
!
interface Loopback0
description PROVIDER-LOOPBACK
ip address 100.120.0.1 255.255.255.255
ip pim nbma-mode
ip pim sparse-mode
ip igmp join-group 232.0.0.1 source 100.120.0.1
!
interface Loopback1
description PROVIDER-ANYCAST-RP
ip address 100.120.1.1 255.255.255.255
ip pim sparse-mode
!
interface Loopback100000
description CUST-00000 INTERCONNECT
vrf forwarding CUST-00000
ip address 192.168.0.1 255.255.255.255
ip pim sparse-dense-mode
ip igmp join-group 226.0.0.1
shutdown
!
interface Loopback200000
description CUST-00000 ANYCAST RP
vrf forwarding CUST-00000
ip address 192.168.0.0 255.255.255.255
ip pim nbma-mode
ip pim sparse-dense-mode
shutdown
!
interface Tunnel11
description CORE-1 PRIMARY DMVPN TUNNEL
ip address 100.122.0.1 255.255.192.0
no ip redirects
ip mtu 1400
ip pim dr-priority 4294967294
ip pim nbma-mode
ip pim sparse-mode
ip nhrp authentication NOI-KEY
ip nhrp network-id 11
ip tcp adjust-mss 1360
cdp enable
ipv6 mtu 1400
ipv6 tcp adjust-mss 1340
ipv6 nhrp authentication NOI-KEY
ipv6 nhrp network-id 11
mpls bgp forwarding
llp nhrp map multicast dynamic
tunnel source GigabitEthernet1
tunnel mode gre multipoint
tunnel key 11
tunnel vrf FRONT-DOOR
!
interface Tunnel12
description CORE-1 SECONDARY DMVPN TUNNEL
ip address 100.122.64.1 255.255.192.0
no ip redirects
ip mtu 1400
ip pim dr-priority 10
ip pim nbma-mode
ip pim sparse-mode
ip nhrp authentication NOI-KEY
ip nhrp network-id 12
ip tcp adjust-mss 1360
shutdown
cdp enable
ipv6 mtu 1400
ipv6 tcp adjust-mss 1340
ipv6 nhrp authentication NOI-KEY
ipv6 nhrp network-id 12
mpls bgp forwarding
llp nhrp map multicast dynamic
tunnel source GigabitEthernet1
tunnel mode gre multipoint
tunnel key 12
tunnel vrf FRONT-DOOR
tunnel protection ipsec profile IPSEC-PROF-DMVPN shared
!
interface Tunnel1122
description GRE TUNNEL to CORE-2
ip address 100.120.255.1 255.255.255.252
no ip redirects
ip mtu 1452
ip pim sparse-mode
shutdown
cdp enable
mpls bgp forwarding
tunnel source GigabitEthernet1
tunnel destination 23.149.104.21
tunnel vrf FRONT-DOOR
tunnel protection ipsec profile IPSEC-PROF-STATIC
!
interface GigabitEthernet1
ip vrf forwarding FRONT-DOOR
ip address 23.149.104.20 255.255.255.224
negotiation auto
vrrp 12 description VRRP-FOR-NMS
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 100.120.255.130 255.255.255.240
ip pim sparse-dense-mode
ip igmp version 3
negotiation auto
vrrp 12 description VRRP-FOR-NMS
vrrp 12 ip 100.120.255.129
vrrp 12 priority 110
no mop enabled
no mop sysid
!
interface GigabitEthernet3
vrf forwarding CUST-00000
ip address 192.168.255.1 255.255.255.252
ip pim sparse-dense-mode
negotiation auto
cdp enable
no mop enabled
no mop sysid
!
router bgp 64512
bgp router-id interface Loopback0
bgp log-neighbor-changes
bgp listen range 100.120.255.0/30 peer-group HUB
bgp listen range 100.120.0.0/14 peer-group SPOKES
neighbor SPOKES peer-group
neighbor SPOKES remote-as 64512
neighbor SPOKES ebgp-multihop 255
neighbor SPOKES transport connection-mode passive
neighbor SPOKES update-source Loopback0
neighbor HUB peer-group
neighbor HUB remote-as 64512
neighbor 100.120.255.2 remote-as 64512
neighbor 100.120.255.2 peer-group HUB
!
address-family ipv4
network 0.0.0.0
redistribute connected
neighbor SPOKES activate
neighbor SPOKES send-community both
neighbor SPOKES route-reflector-client
neighbor SPOKES next-hop-self all
neighbor SPOKES send-label
neighbor HUB activate
neighbor HUB send-community both
neighbor HUB next-hop-self
neighbor HUB send-label
neighbor 100.120.255.2 activate
exit-address-family
!
address-family vpnv4
neighbor SPOKES activate
neighbor SPOKES send-community both
neighbor SPOKES route-reflector-client
neighbor SPOKES next-hop-self all
neighbor HUB activate
neighbor HUB send-community both
neighbor 100.120.255.2 activate
exit-address-family
!
address-family ipv4 mdt
neighbor SPOKES activate
neighbor SPOKES send-community both
neighbor SPOKES next-hop-self all
neighbor HUB activate
neighbor HUB send-community both
neighbor HUB next-hop-self all
exit-address-family
!
address-family ipv4 vrf CUST-00000
redistribute connected route-map CUST-00000-ROUTES
redistribute static route-map CUST-00000-ROUTES
exit-address-family
!
ip forward-protocol nd
!
ip pim rp-address 100.120.1.1 override
ip pim send-rp-announce Loopback1 scope 32 group-list 10
ip pim vrf CUST-00000 rp-address 192.168.255.255 override
ip pim vrf CUST-00000 register-source Loopback100000
ip msdp peer 100.120.0.2 connect-source Loopback0
ip msdp cache-sa-state
ip msdp originator-id Loopback0
ip msdp vrf CUST-00000 peer 192.168.0.2 connect-source Loopback100000
ip msdp vrf CUST-00000 cache-sa-state
ip msdp vrf CUST-00000 originator-id Loopback100000
no ip http server
no ip http secure-server
ip http client source-interface Loopback0
ip route 0.0.0.0 0.0.0.0 Null0
ip route vrf CUST-00000 192.168.255.255 255.255.255.255 192.168.255.2
ip route vrf FRONT-DOOR 0.0.0.0 0.0.0.0 23.149.104.1
ip ssh bulk-mode 131072
ip ssh time-out 60
ip ssh authentication-retries 2
ip ssh pubkey-chain
username bryan
key-hash ssh-rsa FD61A6D6FFD817666D6E420C5E7029CB
key-hash ssh-ed25519 286A947512A7C2CB9B1E0FAF2D61998B bryan@bryanfields.net
!
ip access-list standard CUST-00000-NEXT-HOP-SELF-ACL
10 permit 192.168.0.0 0.0.0.255
20 permit 192.168.255.0 0.0.0.255
ip access-list standard VTY
10 permit 192.168.0.0 0.0.255.255
20 permit 100.64.0.0 0.63.255.255
30 permit 44.98.0.0 0.0.255.255
40 permit 199.47.174.0 0.0.0.255
50 permit 23.149.104.0 0.0.0.255
60 permit 100.120.255.128 0.0.0.7
ip access-list standard snmp-acl
10 permit 100.120.255.128 0.0.0.7
!
ip access-list standard 10
10 permit 224.0.0.0 15.255.255.255
ip access-list standard 20
10 deny 224.0.1.39
20 deny 224.0.1.40
30 permit 224.0.0.0 15.255.255.255
ip access-list extended 2000
10 permit igmp any any
20 permit pim any any
30 permit icmp any any
!
route-map CUST-00000-ROUTES permit 10
match ip address CUST-00000-NEXT-HOP-SELF-ACL
set ip next-hop 100.120.0.1
!
snmp-server group radio v3 priv access snmp-acl
snmp-server trap-source Loopback0
snmp-server source-interface informs Loopback0
snmp ifmib ifindex persist
!
!
!
!
!
control-plane
!
!
mgcp behavior rsip-range tgcp-only
mgcp behavior comedia-role none
mgcp behavior comedia-check-media-src disable
mgcp behavior comedia-sdp-force disable
!
mgcp profile default
!
!
!
!
!
!
line con 0
stopbits 1
line aux 0
line vty 0
access-class VTY in vrf-also
exec-timeout 180 0
transport input ssh
line vty 1
access-class VTY in vrf-also
exec-timeout 180 0
length 0
transport input ssh
line vty 2 4
access-class VTY in vrf-also
exec-timeout 180 0
transport input ssh
line vty 5 15
access-class VTY in vrf-also
exec-timeout 180 0
transport input ssh
line vty 16 97
access-class VTY in vrf-also
transport input ssh
!
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
ntp logging
ntp source GigabitEthernet1
ntp server vrf FRONT-DOOR 45.79.214.107
ntp server vrf FRONT-DOOR 138.236.128.36
ntp server vrf FRONT-DOOR 50.205.57.38
ntp server vrf FRONT-DOOR 144.202.41.38
end
Bryan
version 17.9 service timestamps debug datetime msec service timestamps log datetime msec service call-home platform qfp utilization monitor load 80 platform punt-keepalive disable-kernel-core ! hostname bryan-ir1101 ! boot-start-marker boot system flash bootflash:ir1101-universalk9.17.09.06.SPA.bin boot-end-marker ! ! vrf definition CUST-00000 description Customer 00000 - Mvpn for DAMM radios rd 64512:0 route-target export 64512:100000 route-target import 64512:100000 ! address-family ipv4 mdt default 232.0.1.69 mdt mtu 1400 bgp next-hop Loopback0 exit-address-family ! aaa new-model ! ! aaa authentication login default local aaa authentication login vpnclient local aaa authorization console aaa authorization config-commands aaa authorization exec default local aaa authorization network localgroups local ! ! aaa session-id common ! ip vrf FRONT-DOOR description Front-Door VRF only for public rd 62000:1 ! ip multicast-routing distributed ip multicast-routing vrf CUST-00000 distributed ! ! ! ! ! ! ip name-server vrf FRONT-DOOR 1.1.1.1 no ip domain lookup ip domain name keekles.org ! ip dhcp pool CUST-00000-00 vrf CUST-00000 network 192.168.4.0 255.255.255.0 default-router 192.168.4.1 dns-server 1.1.1.1 lease 0 0 15 ! ! ! login block-for 60 attempts 3 within 30 login delay 3 login on-failure log login on-success log ipv6 unicast-routing ! no mpls ip propagate-ttl multilink bundle-name authenticated ! ! license feature hseck9 license udi pid IR1101-K9 sn FCW22260069 license boot level network-advantage license smart transport callhome archive log config record rc logging enable logging size 400 path bootflash:archive/ maximum 14 memory free low-watermark processor 45309 ! diagnostic bootup level minimal ! spanning-tree extend system-id ! ! ! username nnnnnn privilege 15 secret 9 ! redundancy ! crypto ikev2 proposal IKEv2-VPN encryption aes-cbc-256 integrity sha512 group 19 ! crypto ikev2 policy IKEv2-VPN-POLICY match fvrf FRONT-DOOR proposal IKEv2-VPN ! crypto ikev2 keyring NOI-DMVPN peer REMOTE-ROUERS ! peer CORE-1 description CORE-1 address 23.149.104.20 pre-shared-key <PSK> ! peer CORE-2 description CORE-2 address 23.149.104.21 pre-shared-key <PSK> ! ! ! crypto ikev2 profile IKEv2-VPN-PROFILE match fvrf FRONT-DOOR match identity remote address 23.149.104.20 255.255.255.255 match identity remote address 23.149.104.21 255.255.255.255 authentication remote pre-share authentication local pre-share keyring local NOI-DMVPN no lifetime certificate ! crypto ipsec transform-set AES256 esp-aes 256 esp-sha512-hmac mode transport ! crypto ipsec profile IPSEC-PROF-DMVPN set transform-set AES256 set ikev2-profile IKEv2-VPN-PROFILE ! interface Loopback0 ip address 100.120.0.64 255.255.255.255 ip pim sparse-mode ip igmp join-group 224.1.1.10 ! interface Tunnel11 ip address 100.122.0.64 255.255.192.0 no ip redirects ip mtu 1400 ip pim dr-priority 0 ip pim sparse-mode ip nhrp authentication NOI-KEY ip nhrp map 100.122.0.1 23.149.104.20 ip nhrp map multicast 23.149.104.20 ip nhrp network-id 11 ip nhrp nhs 100.122.0.1 ip tcp adjust-mss 1360 cdp enable ipv6 enable ipv6 mtu 1400 ipv6 tcp adjust-mss 1340 ipv6 nhrp authentication NOI-KEY ipv6 nhrp network-id 11 mpls bgp forwarding llp nhrp map multicast 23.149.104.20 tunnel source GigabitEthernet0/0/0 tunnel destination 23.149.104.20 tunnel key 11 tunnel vrf FRONT-DOOR ! interface Tunnel12 no ip address ip pim sparse-mode ! interface Tunnel21 ip address 100.123.0.64 255.255.192.0 no ip redirects ip mtu 1400 ip pim sparse-mode ip nhrp authentication NOI-KEY ip nhrp map 100.123.0.1 23.149.104.21 ip nhrp map multicast 23.149.104.21 ip nhrp network-id 21 ip nhrp nhs 100.123.0.1 ip tcp adjust-mss 1360 shutdown cdp enable ipv6 enable ipv6 mtu 1400 ipv6 tcp adjust-mss 1340 ipv6 nhrp authentication NOI-KEY ipv6 nhrp network-id 21 mpls bgp forwarding llp nhrp map multicast 23.149.104.21 tunnel source GigabitEthernet0/0/0 tunnel destination 23.149.104.21 tunnel key 21 tunnel vrf FRONT-DOOR tunnel protection ipsec profile IPSEC-PROF-DMVPN ikev2-profile IKEv2-VPN-PROFILE ! interface GigabitEthernet0/0/0 ip vrf forwarding FRONT-DOOR ip address dhcp ip nat outside ipv6 dhcp client request vendor ipv6 address autoconfig default ! interface FastEthernet0/0/1 switchport access vlan 100 switchport mode access ! interface FastEthernet0/0/2 ! interface FastEthernet0/0/3 ! interface FastEthernet0/0/4 ! interface Cellular0/1/0 ip address negotiated ip tcp adjust-mss 1460 dialer in-band dialer idle-timeout 0 dialer watch-group 1 ipv6 address dhcp ipv6 enable pulse-time 1 ! interface Cellular0/1/1 no ip address shutdown ! interface Vlan1 no ip address ! interface Vlan100 vrf forwarding CUST-00000 ip address 192.168.4.1 255.255.255.0 ip pim sparse-dense-mode ip igmp join-group 226.0.0.64 ip igmp version 3 no autostate ! interface Async0/2/0 no ip address encapsulation scada ! interface vasileft1 vrf forwarding CUST-00000 ip address 100.126.1.1 255.255.255.248 ip nat inside no keepalive ! interface vasiright1 ip vrf forwarding FRONT-DOOR ip address 100.126.1.2 255.255.255.248 ip nat inside no keepalive ! router bgp 64512 bgp router-id interface Loopback0 bgp log-neighbor-changes neighbor 100.120.0.1 remote-as 64512 neighbor 100.120.0.1 ebgp-multihop 255 neighbor 100.120.0.1 update-source Loopback0 neighbor 100.122.0.1 remote-as 64512 neighbor 100.122.0.1 ebgp-multihop 255 neighbor 100.123.0.1 remote-as 64512 neighbor 100.123.0.1 shutdown neighbor 100.123.0.1 ebgp-multihop 255 ! address-family ipv4 network 100.120.0.0 mask 255.252.0.0 redistribute connected no neighbor 100.120.0.1 activate neighbor 100.122.0.1 activate neighbor 100.122.0.1 send-label neighbor 100.123.0.1 activate neighbor 100.123.0.1 send-label exit-address-family ! address-family ipv4 mvpn exit-address-family ! address-family vpnv4 neighbor 100.122.0.1 activate neighbor 100.122.0.1 send-community both neighbor 100.123.0.1 activate neighbor 100.123.0.1 send-community both exit-address-family ! address-family vpnv4 multicast exit-address-family ! address-family ipv4 mdt neighbor 100.120.0.1 activate neighbor 100.120.0.1 send-community both neighbor 100.122.0.1 activate neighbor 100.122.0.1 send-community extended neighbor 100.123.0.1 activate neighbor 100.123.0.1 send-community extended exit-address-family ! address-family ipv4 vrf CUST-00000 redistribute connected route-map CUST-00000-ROUTES exit-address-family ! ip forward-protocol nd no ip http server ip http auth-retry 3 time-window 1 ip http authentication local ip http secure-server ip pim rp-address 100.120.1.1 override ip pim vrf CUST-00000 rp-address 192.168.255.255 override ip pim vrf CUST-00000 send-rp-announce Vlan100 scope 32 group-list 10 ip pim vrf CUST-00000 send-rp-discovery Vlan100 scope 32 ip pim vrf CUST-00000 register-source BDI100 ip nat inside source list CUST-00000-NAT interface GigabitEthernet0/0/0 vrf FRONT-DOOR overload ip route vrf CUST-00000 0.0.0.0 0.0.0.0 vasileft1 100.126.1.2 ip route vrf FRONT-DOOR 192.168.4.0 255.255.255.0 vasiright1 100.126.1.1 ip route vrf FRONT-DOOR 0.0.0.0 0.0.0.0 dhcp ip ssh time-out 60 ip ssh authentication-retries 2 ip ssh version 2 ip ssh pubkey-chain username <USER> key-hash ssh-ed25519 <hash> ! ! ip access-list standard CUST-00000-ROUTE-ACL 10 permit 192.168.0.0 0.0.255.255 ip access-list standard VTY 10 permit 192.168.0.0 0.0.255.255 20 permit 100.64.0.0 0.63.255.255 30 permit 44.98.0.0 0.0.255.255 40 permit 199.47.174.0 0.0.0.255 50 permit 23.149.104.0 0.0.0.255 60 permit 100.120.255.128 0.0.0.7 ip access-list standard snmp-acl 10 permit 100.120.255.128 0.0.0.7 ! ip access-list extended CUST-00000-NAT 10 permit ip 192.168.4.0 0.0.0.255 any ! ip access-list standard 1 10 permit any ip access-list standard 10 10 permit 224.0.0.0 15.255.255.255 ip access-list standard 20 10 deny 224.0.1.39 20 deny 224.0.1.40 30 permit 224.0.0.0 15.255.255.255 ip access-list extended 101 10 permit ip any host 23.149.104.20 dialer watch-list 1 ip 5.6.7.8 255.255.255.255 dialer watch-list 1 delay route-check initial 60 dialer-list 1 protocol ip list 1 ! route-map CUST-00000-ROUTES permit 10 match ip address CUST-00000-ROUTE-ACL ! snmp-server group radio v3 priv access snmp-acl snmp-server trap-source Loopback0 snmp-server source-interface informs Loopback0 snmp ifmib ifindex persist ! line con 0 stopbits 1 speed 115200 line 0/0/0 line 0/2/0 line vty 0 4 access-class VTY in vrf-also exec-timeout 180 0 transport input all line vty 5 97 access-class VTY in vrf-also exec-timeout 180 0 transport input all line vty 98 817 exec-timeout 180 0 transport input all ! call-home ! If contact email address in call-home is configured as sch-smart-licensing@cisco.com ! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications. contact-email-addr sch-smart-licensing@cisco.com source-interface GigabitEthernet0/0/0 profile "CiscoTAC-1" active destination transport-method http ntp logging ntp master ntp server vrf FRONT-DOOR 45.79.214.107 ntp server vrf FRONT-DOOR 138.236.128.36 ntp server vrf FRONT-DOOR 162.248.241.94 ntp server vrf FRONT-DOOR 172.104.193.207 ntp server vrf FRONT-DOOR ip pool.ntp.org end